Introduction
Most collaboration platforms claim to offer encrypted messaging, yet the depth and structure of that encryption can vary significantly from one vendor to another. While marketing pages often highlight security badges and technical terminology, decision-makers in the evaluation stage need far more than surface-level assurances. When teams are narrowing down vendors, comparing encrypted messaging capabilities becomes a strategic exercise that directly impacts data protection, compliance posture, and long-term operational risk.
This guide is designed for professionals who already understand what encrypted messaging is and why it matters. The focus here is not on explaining encryption basics but on helping you compare implementations across collaboration platforms in a structured and practical way. By the end, you will have a clear framework for evaluating architecture, governance, coverage scope, compliance readiness, and vendor transparency before committing to a platform.
Why Comparing Encrypted Messaging Features Requires More Than a Feature List
Vendor comparison tables often reduce encrypted messaging to a simple checkbox. On paper, many platforms appear equivalent because they all claim to encrypt messages. However, the underlying architecture, key management policies, scope of coverage, and regulatory alignment can differ in ways that are not immediately visible.
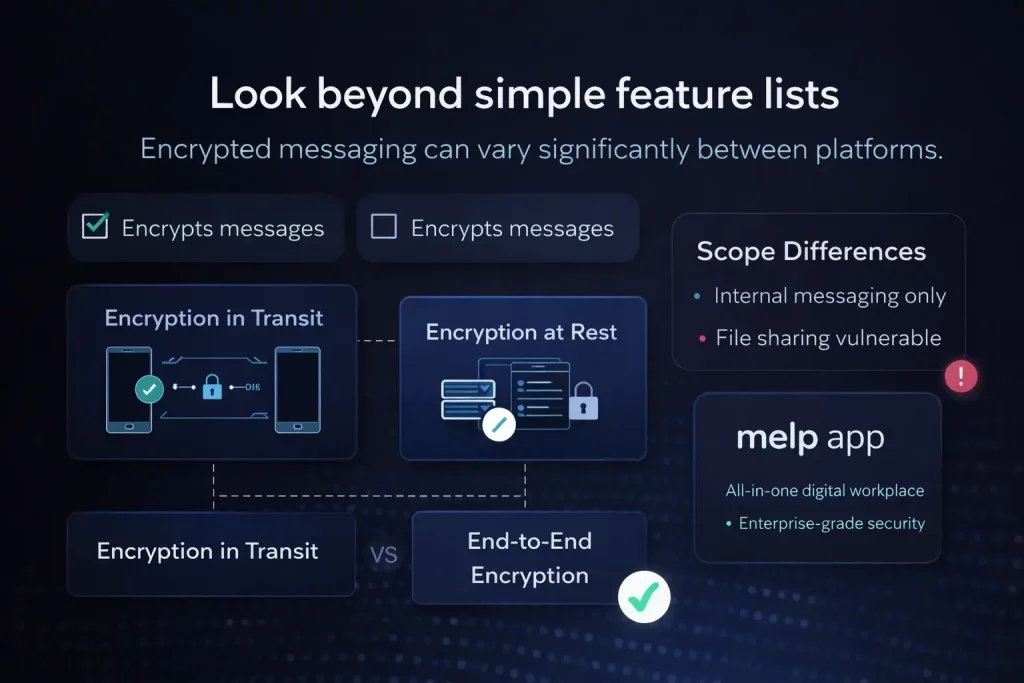
A superficial comparison can create blind spots. For example, two tools may both advertise encrypted messaging, but one may only encrypt data in transit while the other provides end-to-end encryption. Similarly, one platform may secure internal chats but leave external collaboration channels under a different security model. These differences are rarely obvious in marketing summaries, yet they carry meaningful implications for compliance audits and risk exposure.
To make an informed decision, organizations must move beyond feature lists and examine the structural dimensions that define how encrypted messaging is actually implemented. A structured comparison framework helps ensure that the chosen platform aligns with both security requirements and long-term collaboration needs.
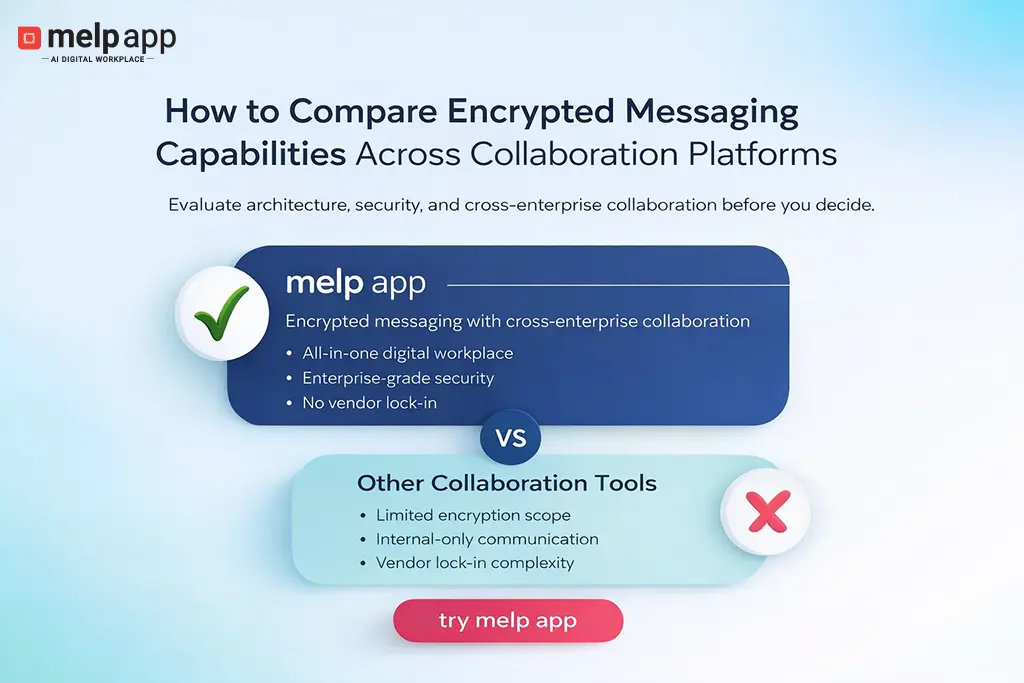
If secure encrypted messaging is a priority for your organization, explore how melp app protects internal and external collaboration within one unified workspace. Sign up today and experience enterprise-grade security with HIPAA, GDPR, ISO 27001, SOC 2 readiness, and multi-factor authentication built directly into your communication layer.
Core Dimensions to Compare Encrypted Messaging Across Platforms
Meaningful comparison requires examining several dimensions of encrypted messaging implementation. These include encryption architecture, key management control, scope of coverage, regulatory alignment, and transparency practices. Each dimension reveals whether security is deeply embedded in the platform or layered on as a feature.
Encryption Model Architecture
The first comparison point is the encryption model itself. Many collaboration tools implement encryption in transit, which protects data as it travels between a user’s device and the platform’s servers. This is a baseline security measure and is widely adopted. However, encryption in transit alone does not prevent server-side visibility.
Encryption at rest protects stored data within the vendor’s infrastructure. While this adds another layer of protection, it still typically allows the service provider to access decrypted data under certain circumstances.
End-to-end encryption, by contrast, ensures that only the communicating parties can read the messages. In this model, decryption keys remain with users rather than the vendor. When comparing encrypted messaging capabilities, it is critical to understand which model is being used and whether the platform clearly documents its architecture.
Decision-makers should request technical documentation that explains how messages are encrypted, where keys are stored, and under what conditions data can be accessed. Without this level of clarity, the term encrypted messaging remains too broad to support a confident evaluation.
Key Management and Control
Key management is often overlooked during comparison, yet it plays a central role in encrypted messaging governance. Even when encryption is implemented, the entity that controls the keys ultimately controls access.
Some platforms manage encryption keys entirely within their own infrastructure. While this simplifies deployment, it may raise concerns for organizations that require stronger control over sensitive data. Other platforms offer customer-managed keys, allowing organizations to retain greater authority over encryption lifecycles. Bring-your-own-key models go a step further by enabling enterprises to generate and manage keys independently.
When comparing vendors, evaluate how keys are generated, rotated, stored, and revoked. Ask whether the platform supports granular control and whether administrators can audit key usage. Key ownership affects not only security posture but also regulatory compliance and legal defensibility in the event of disputes.
Scope of Encryption Coverage
Encrypted messaging comparison must also account for scope. Some platforms encrypt chat messages but apply different policies to file attachments, shared links, or metadata. Others may protect internal communication channels while handling external collaboration differently.
Modern organizations rarely operate in isolation. Vendors, partners, contractors, and clients frequently interact within shared digital environments. Many collaboration platforms, such as Google, Microsoft, and Slack, focus primarily on securing internal team communication. However, today’s distributed businesses depend heavily on cross-enterprise collaboration where vendors, clients, and contractors operate within shared workspaces.
melp app operates on a multi-enterprise linking platform model, enabling structured collaboration across internal and external stakeholders within a unified digital workplace. This broader collaboration model highlights why scope comparison matters. If encrypted messaging is limited to internal teams, organizations may unknowingly expose sensitive conversations when engaging external participants.
During evaluation, confirm whether encryption policies remain consistent across internal and external channels, file sharing, and collaborative workspaces. A fragmented approach to encryption can create inconsistent protection levels across the organization.
Compliance Alignment and Regulatory Readiness
Encrypted messaging does not exist in isolation from compliance requirements. Enterprises operating in regulated industries must ensure that collaboration platforms align with standards such as SOC 2 and GDPR. In healthcare or financial environments, additional frameworks may apply.
When comparing platforms, assess whether the vendor provides documentation supporting compliance audits. Examine data residency controls, especially if your organization operates across multiple jurisdictions. Understand how the platform handles data retention, deletion requests, and breach notifications.
Compliance readiness is not solely about certifications. It involves understanding how encrypted messaging integrates into broader governance processes. If encryption practices conflict with regulatory obligations, the organization may face exposure despite technical safeguards.
According to the 2025 Verizon Data Breach Investigations Report (DBIR), 75 percent of system intrusion breaches involved ransomware, and 88 percent of basic web application breaches involved stolen credentials. The report also highlights that third-party involvement in breaches has doubled compared to last year, emphasizing how interconnected business ecosystems increase exposure risk.
Security Transparency and Independent Validation
Transparency is a strong indicator of vendor maturity. Platforms that invest in encrypted messaging typically publish security whitepapers, undergo independent audits, and provide detailed documentation outlining their architecture.
When comparing vendors, evaluate how openly they discuss security practices. Do they provide access to audit reports under non-disclosure agreements? Do they maintain clear incident disclosure policies? Are updates to encryption protocols communicated transparently?
A vendor’s willingness to share documentation reflects confidence in its implementation. Limited or vague explanations may signal that encrypted messaging is treated as a marketing feature rather than a foundational design principle.
A Real-World Comparison Scenario
Consider the experience of Michael, an IT director at a mid-sized consulting firm. While comparing collaboration platforms, he focused primarily on user interface and pricing. Both shortlisted vendors claimed to offer encrypted messaging, and the feature appeared identical in summary charts.
After deployment, Michael discovered that external partner channels were not covered under the same encryption model as internal chats. Sensitive project discussions with contractors were stored under a different policy, creating confusion during a compliance review. Although no breach occurred, the audit revealed documentation gaps that required additional remediation efforts.
Michael’s experience highlights how shallow comparison can create hidden risk. If he had evaluated encryption architecture, key management policies, and scope coverage more carefully, the issue would have surfaced before implementation. Structured comparison protects not only data but also operational stability.
Encrypted Messaging Comparison Checklist
To simplify your evaluation process, use the following checklist when comparing collaboration platforms:
• Identify whether encryption is in transit, at rest, or end-to-end
• Clarify who controls encryption keys and how they are managed
• Confirm that encryption policies extend to external collaboration channels
• Review compliance certifications and data residency controls
• Request access to security documentation and audit summaries
This checklist supports consistent, evidence-based comparison rather than relying on marketing claims.
Strategic Considerations Before Final Selection
Beyond technical features, encrypted messaging comparison should include strategic foresight. Collaboration needs often expand over time as organizations grow or integrate new partners. A platform that meets current requirements may not scale effectively if encryption coverage is limited or difficult to extend.
Vendor lock-in is another consideration. If key management or encryption configurations are tightly bound to proprietary systems, transitioning away from the platform later may introduce complexity. Evaluate how portable your data and encryption controls would be in a migration scenario.
Long-term risk exposure should also factor into the decision. Encrypted messaging is not just a feature that enhances user privacy. It is part of a broader risk management framework that affects legal defensibility, client trust, and brand reputation. Platforms that treat encryption as a core architectural principle are more likely to adapt to evolving security standards.
As regulatory environments shift and cyber threats become more sophisticated, the depth of encrypted messaging implementation becomes increasingly important. Selecting a platform with robust and transparent encryption practices supports resilience rather than reactive remediation.
Why Enterprises Choose melp app for Secure Encrypted Messaging
Enterprises choose melp app for secure, encrypted messaging because it is designed as a multi-enterprise linking platform that protects communication not only within teams but also across external stakeholders. Unlike basic chat tools, melp app integrates encrypted messaging into a broader AI-powered digital workplace where internal teams, vendors, clients, and partners collaborate inside a unified and structured environment. This architecture reduces communication silos and ensures that sensitive conversations remain protected across the entire collaboration network.
Encrypted messaging in melp app is supported by enterprise-grade security controls, including HIPAA, GDPR, ISO 27001, SOC 2 compliance readiness, and multi-factor authentication. These controls strengthen data protection across chats, file sharing, document management, and video communication. Because encrypted messaging is embedded across the platform’s communication layer, enterprises can securely conduct meetings with breakout rooms, use AI summarization, share files through MELP Drive, and manage documents without compromising confidentiality.
Enterprises also value that melp app combines encrypted messaging with localization support, allowing the full workspace to adapt to the user’s preferred language, which strengthens secure collaboration across global teams. With features such as personal rooms, face centering in video meetings, integrations with Asana and Salesforce, and structured evaluation modes for interviews, melp app provides a secure alternative to fragmented tools like Zoom, Microsoft Teams, Google Workspace, and Slack. This integrated and compliance-aligned approach is why enterprises consider melp app a strong choice when encrypted messaging is a core decision factor.
Conclusion
Comparing encrypted messaging capabilities across collaboration platforms requires more than checking a feature box. The true differences emerge when evaluating architecture, key management, scope coverage, compliance alignment, and vendor transparency. Each of these dimensions reveals whether encryption is implemented as a foundational safeguard or positioned as a surface-level enhancement.
For organizations in the consideration stage, structured comparison reduces uncertainty and prevents costly oversights. By asking precise questions and reviewing documentation carefully, decision-makers can align platform selection with governance requirements and long-term collaboration goals.
Encrypted messaging should be evaluated as a strategic risk management decision rather than a convenience feature. The platform you choose will shape how securely your teams communicate, collaborate, and engage with external stakeholders in the years ahead. Taking the time to compare capabilities thoughtfully ensures that your collaboration environment supports both productivity and sustained security.
Ready to move to a secure digital workplace? Create your melp app account in seconds and continue with Google, Microsoft, or your work email. Start collaborating in a protected environment designed for encrypted messaging, compliance, and scalable enterprise communication.